Mobile Security
- Home
- Mobile Security
Gain Full Visibility And Control Over Mobile User Activity
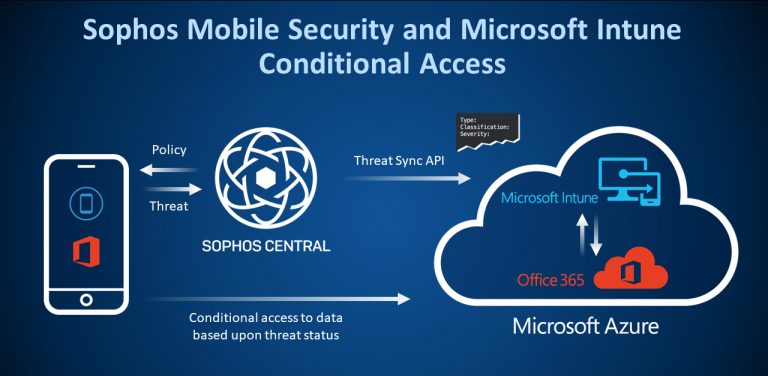
Improved capabilities of current mobile devices are converting them from portable email clients to viable desktop replacements and now viewed as the centerpiece of modern information knowledge work. In some cases, such as Windows 10 devices, there is virtually no difference between a tablet and a desktop, except the form factor.
Unfortunately, hackers don’t care about the form factor: From their point of view, mobile devices are just an organization’s desktop, but one that doesn’t have the extensive protection of a corporate perimeter. This makes them easy pickings to be hacked. With increasing numbers of people accessing and creating documents on the go through Office 365 and Google Apps, these devices now have an equal level of access to sensitive corporate information, and thus require equivalent protection.
This includes:
• Anti-malware and/or application whitelisting: Not only are app stores not as safe as they purport, applications can be side-loaded, and vulnerabilities such as Blue-Borne have demonstrated that arbitrary code can be introduced through remote code execution vulnerabilities.
• Encryption of sensitive files: Even when users don’t use tablets and phones to store files, sensitive information can be insecurely cached from email, web and chat programs. Also, users will often download a file for a review and forget that it is in their downloaded files folder. These can easily be used by criminals that either have remote or physical access to the mobile device.
• Remote management capability: Originally known as mobile device management, the ability to push down software and enforce security policy (such as pin/password complexity) remains as relevant today.
Mobile security management needs to treat all of your mobile devices in the same manner as non-mobile devices because they expose the same security risks – if not higher.
If you’re not sure whether your mobile strategy is having a negative impact on your security posture, contact DataSecure Security for an obligation free chat, and review some of our strategies to help you go mobile more safely.



